How To Read Encrypted Whatsapp Messages On Iphone
WhatsApp remains one of the most popular instant messengers. With more than 1.5 billion users and about half billion daily active users, WhatsApp sends over 100 billion messages per day. WhatsApp is secure thanks to end-to-end encryption to make intercepted messages impossible to decrypt. While this is great news to consumers and privacy advocates, it is also bad news for the law enforcement. Once an expert accepts to access the suspect's WhatsApp communication history, they will struggle with the encryption and demand for a vendor-provided backdoor (WhatsApp: The Bad Guys' Secret Weapon).
Are there any other options to access WhatsApp conversations? We know of at least two. The first option is capturing the message database directly from the device of either party. The other option is going through the cloud. WhatsApp does not have its own native cloud service such as Telegram. All it has is a messaging relay service, which does not store messages for any longer than required to pass them along. In other words, any message that passes through WhatsApp servers is immediately deleted once it's delivered (and it would be of no use to forensic experts anyway due to end-to-end encryption). It is important to note that WhatsApp accounts cannot be used on more than one device.
Let's review WhatApp recovery/decryption options for both Android and iOS, and see what is new in Elcomsoft eXplorer for WhatsApp (EXWA).
WhatsApp in Android
On Android smartphones, WhatsApp keeps its chat database in a sandbox. The database is excluded from ADB backups, and can only be accessed if the device is rooted. The only way to access a WhatsApp database on non-rooted devices requires sideloading a special version of WhatsApp and forcing it to return the original, unencrypted database to the host. We can do it with EXWA, but only on older versions of Android from Android 4.0 through 6.0.1. Android 7.0 and newer make things much more complex; we are still looking forward to implement a similar approach for more recent Android builds. In other words, if you are acquiring a reasonably new Android handset, it's not very likely that you'll be able to pull this trick (at least for the time being).
WhatsApp can also create a standalone backup to Android shared storage or an SD card, but such backups are always encrypted. Encrypted WhatsApp backups have file names ending with .cryptNN, where NN is a number. To decrypt that database, you will need the encryption key that is stored in WhatsApp sandbox. This puts us back to the root/no root situation, as sandbox access is only possible if you have superuser permissions. And if you do, you are much better of just pulling the original WhatsApp database from the app's sandbox – unless you need data in that particular backup. The number in the .cryptNN represents the revision of the encryption algorithm that is used to protect the backup. These are very minor changes in encryption algorithms that do not actually affect the security. Open-source code is available to decrypt such files (e.g. here and there), but you still need the encryption key that is not easy to obtain.
Is it possible just to calculate or generate the encryption key instead of extracting yet? We can try. But first let us have a look at WhatsApp backups on Google Drive.
WhatsApp backups that can be created from within the app are optional; you can select a daily, weekly or monthly backup, or just do it by request when you press the [Backup] button. You can also completely disable backups. A backup will always contain chats and pictures (videos are optional), but not contacts. For the Android version of WhatsApp (and so backups on Google Drive) chats are always encrypted, while media files are not.
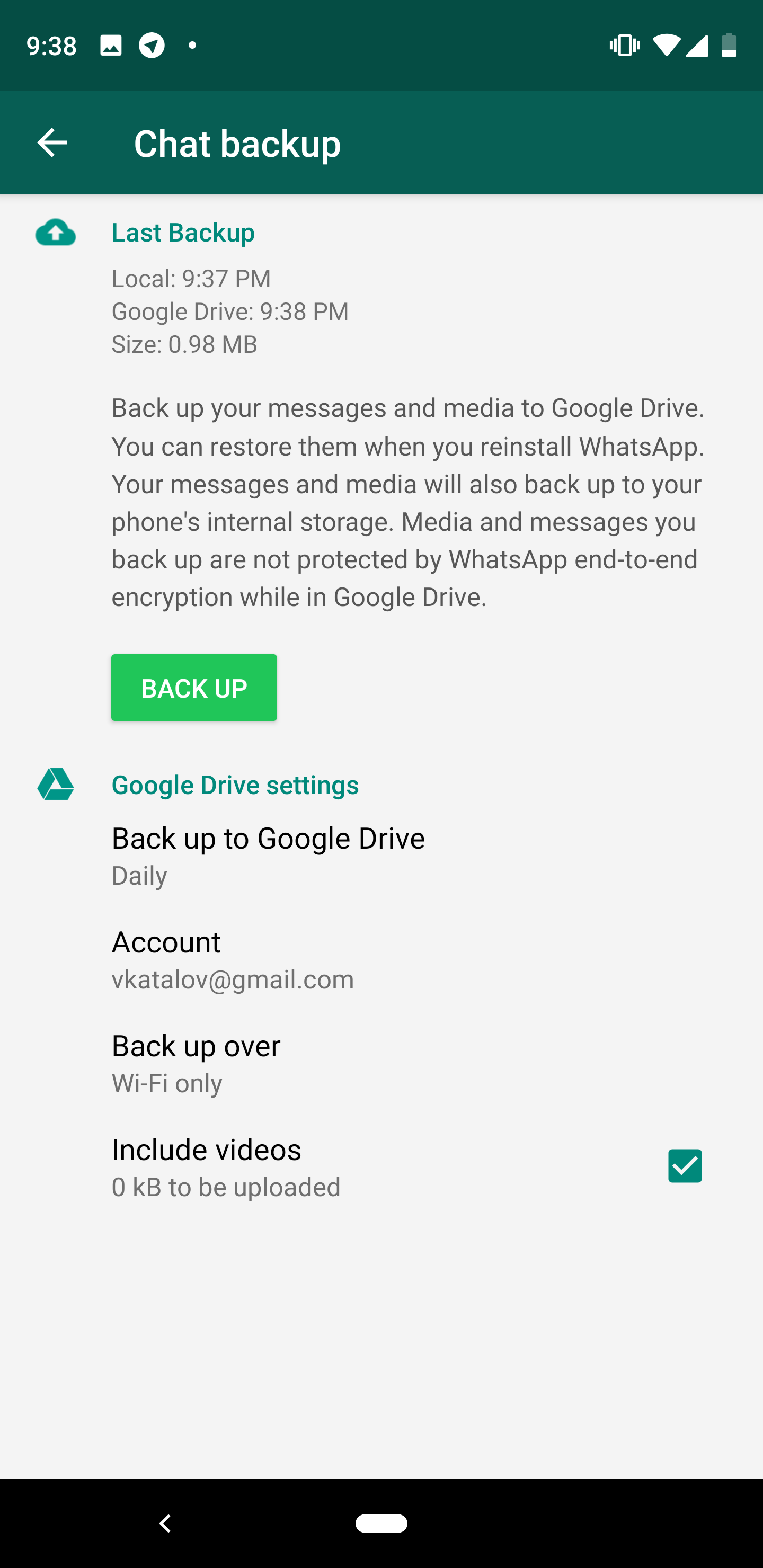
For a long time, EXWA has been able to download WhatsApp backups from Google Drive (of course, if you have the user's Google credentials), see Extract and Decrypt Android WhatsApp Backups from Google Account.
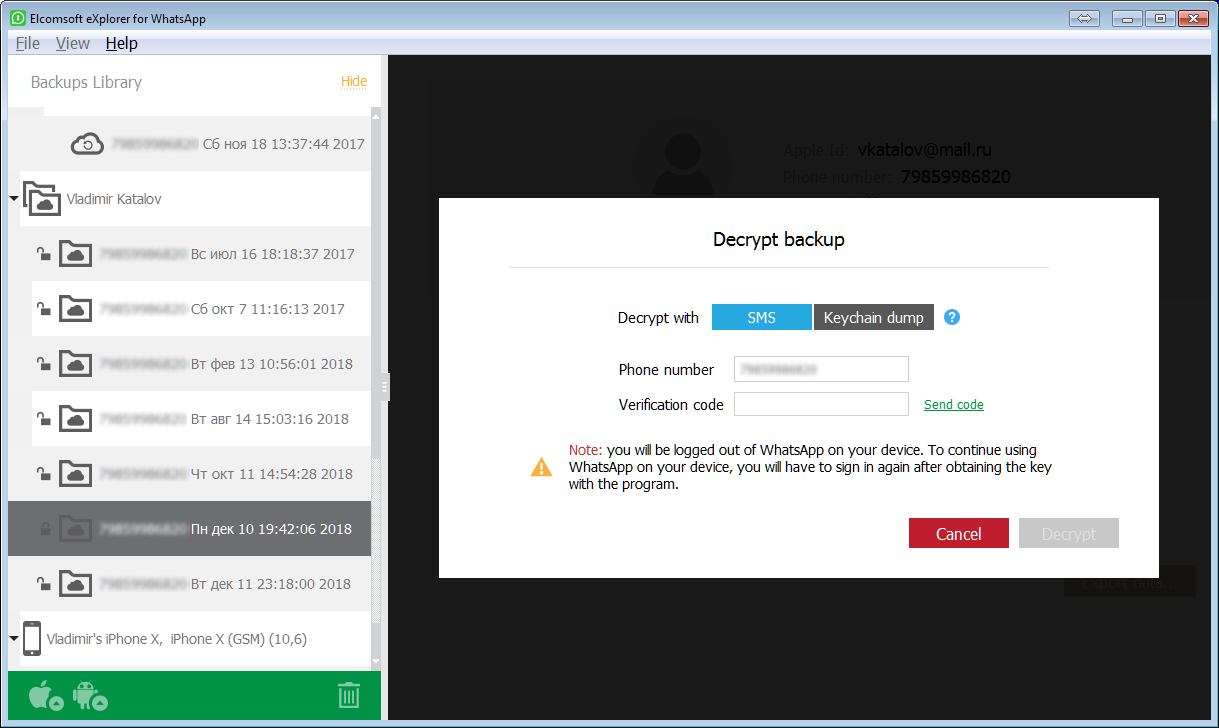
How do we deal with encryption? We do it the same way as WhatsApp itself when restoring from a backup. One will need to obtain a security code by SMS (you will need access to the phone number in order to receive it). The only issue is that once the code is generated on the server, WhatsApp is deactivated on the user's device. Of course, the user can re-activate it again, but the encryption key we generate will work only for backups that were saved before, but not for any future backups.
WhatsApp in iOS
For iOS devices, the easiest way to access WhatsApp conversations is analyzing a local iTunes-style backup. There is no additional encryption for WhatsApp data inside device backups. However, if a backup password is set, one must enter the password, recover it or reset it on the iPhone itself.
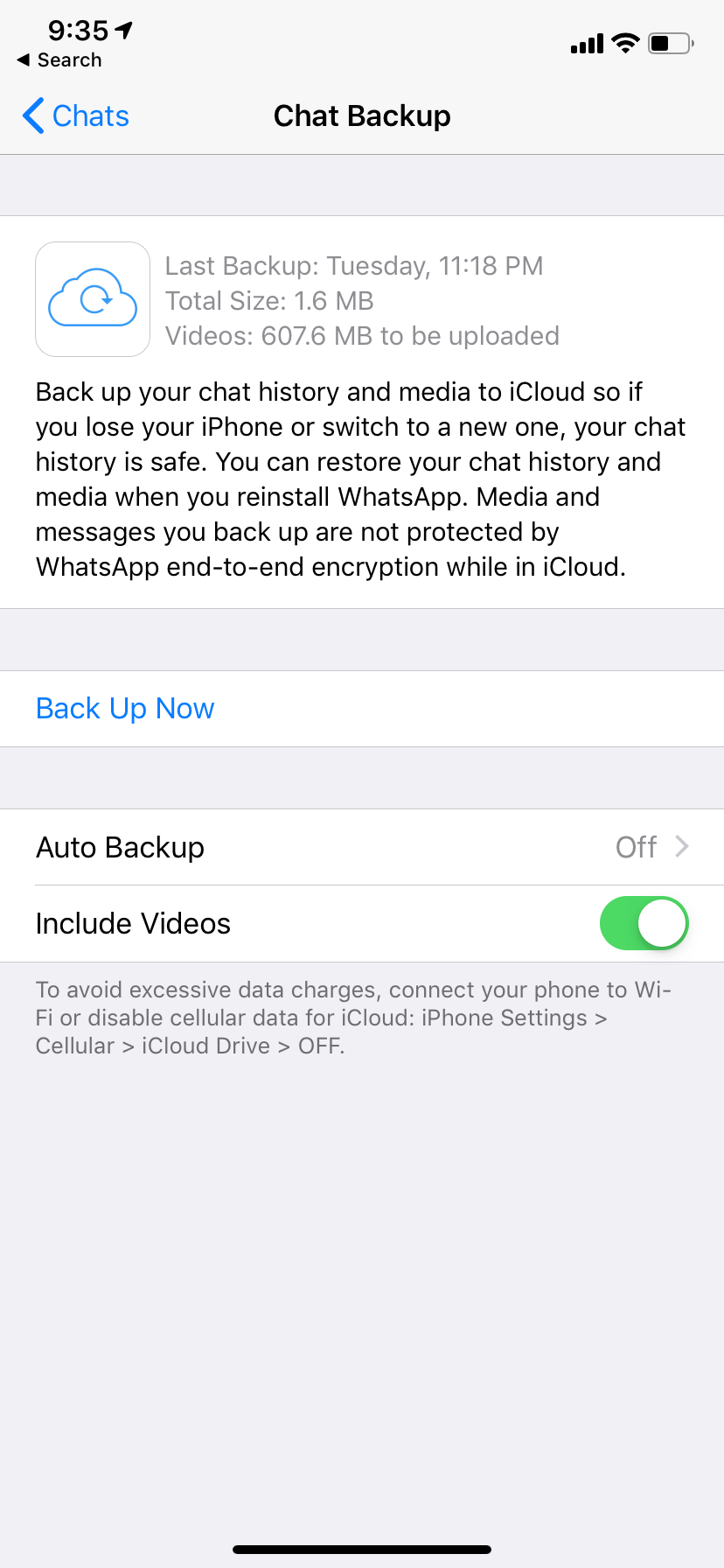
What about iCloud backups? They are essentially the same; WhatsApp chats and media files are saved there as well without any additional encryption. You will need to have the user's iCloud credentials (password plus the second factor, or the authentication token) to download device backups. Once you download a backup, WhatsApp extraction is trivial.
Just like the Android version, WhatsApp for iOS can make standalone backups as well. These are stored in iCloud drive.
WhatsApp standalone backups in iCloud Drive are also encrypted. The protection is similar to backups in Google Drive. EXWA supports these backups as well, see Extract and Decrypt WhatsApp Backups from iCloud.
New in Elcomsoft Extractor for WhatsApp
So what has changed in EXWA? We learned how to obtain the encryption keys directly from the iPhone, and so we can now decrypt WhatsApp standalone iCloud Drive backups without the need for the security code. The user's WhatsApp installation will therefore remain active.
Technically speaking, the encryption key is stored in the keychain. Most keychain items can be easily accessed with Elcomsoft Phone Breaker, just not this one. WhatsApp encryption key targets a higher security class, and so it can be only obtained with iOS Forensic Toolkit 4.0 with Physical Keychain Extraction.
Once you obtain the encryption key and open the WhatsApp backup downloaded from iCloud Drive, you will be prompted for decryption (as we already had it). However, instead of authenticating with WhatsApp servers (to obtain the security code) you are now able to specify path to the keychain file you've extracted with iOS Forensic Toolkit (keychaindump.xml by default).
This is the old method. We request the activation key from WhatsApp:
And this is the new method: you just need the keychain file from a jailbroken iPhone:
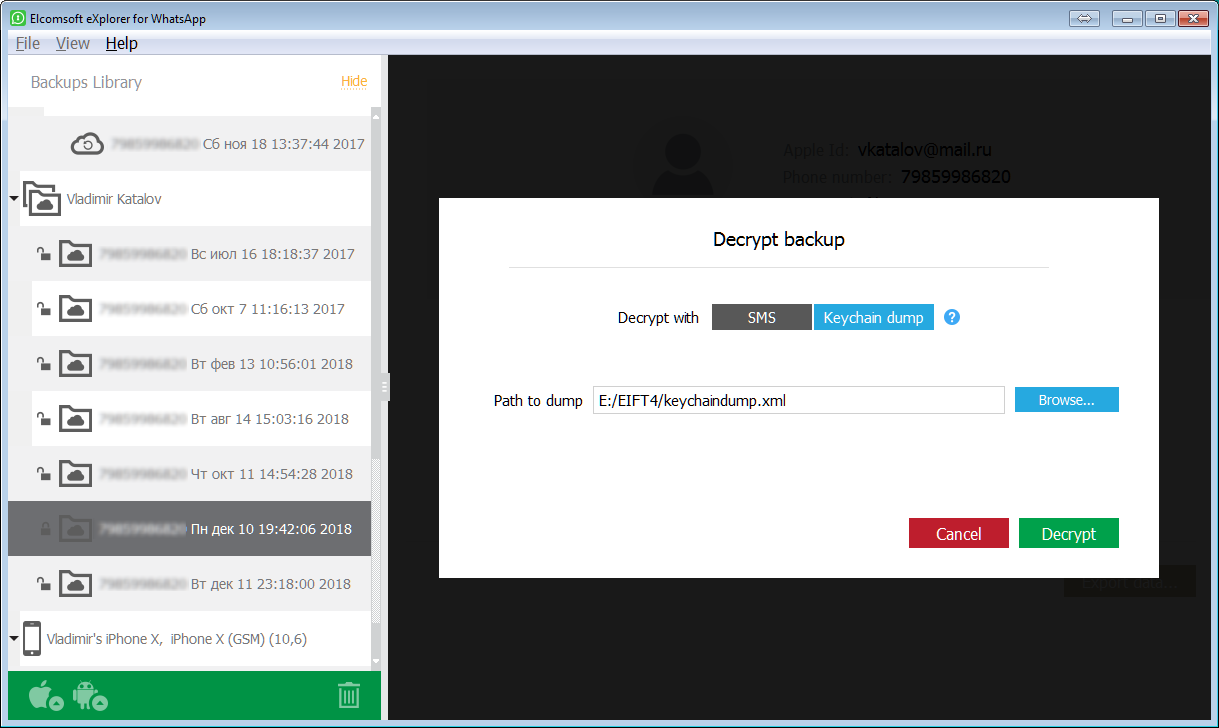
There are multiple benefits to this approach. First, you will no longer require to obtain the security code by SMS or phone call, and WhatsApp will remain active on the user's iPhone. If you don't have access to the user's SIM card, this could be the only extraction method available. In addition, the decryption key will work for all past and future backups.
Why ever bother with iCloud Drive backups if you have the device available? A backup may contain chats that have been already deleted on the device. While you can sometimes recover deleted records from a SQLite database, this is not always the case.
Conclusion
Elcomsoft eXplorer for WhatsApp is the most powerful WhatsApp recovery and decryption tool on the market that supports both iOS and Android versions of WhatsApp and decrypts all types of backups. We will do our best to add even more features; your suggestions are really appreciated. Speaking of which, do you need a macOS version?
REFERENCES:
![]()
Elcomsoft Explorer for WhatsApp
Elcomsoft Explorer for WhatsApp is a tool to download, decrypt and display WhatsApp communication histories. The tool automatically acquires WhatsApp databases from one or multiple sources, processes information and displays contacts, messages, call history and pictures sent and received. The built-in viewer offers convenient searching and filtering, and allows viewing multiple WhatsApp databases extracted from various sources.
Elcomsoft Explorer for WhatsApp official web page & downloads »
How To Read Encrypted Whatsapp Messages On Iphone
Source: https://blog.elcomsoft.com/2018/12/a-new-method-for-decrypting-whatsapp-backups/
Posted by: jantzenprolead.blogspot.com

0 Response to "How To Read Encrypted Whatsapp Messages On Iphone"
Post a Comment